Derek Walkush
A New DeFi Security Paradigm
Security is an existential problem for the sector that needs to be resolved
This was first published as a Twitter thread.
DeFi is entering an entirely new security paradigm: simply put, security measures are going from reactive to proactive. Here are the emerging trends and projects.
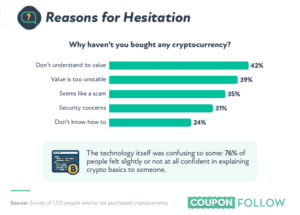
Zooming out, security remains one of the primary bottlenecks for crypto adoptions, particularly in DeFi. A survey earlier this year found it to be one of the primary reasons people don’t invest.
And just over the past 8 months, approximately $2b was lost in hacks. Notable events were Ronin ($616m), Poly Network ($602m), and Wormhole ($326m).
Attacks are becoming more sophisticated, not only exploiting bugs in code but even broader protocol design.
Here’s a high-level and non-exhaustive overview of the current main attack vectors in crypto.
Importantly, as the industry grows, it becomes a bigger and bigger target for hacks. North Korea is likely using state resources to architect these attacks, and only more sophisticated actors should be expected to look at the space.
The current security landscape is quite reactive and passes considerable risk to protocol users.
Projects often audit their contracts and place a few bug bounties. If an attack occurs, they “react” by addressing the exploit and possibly compensating victims.
Every project I speak with complains about the expense and length of audits. There are often wait periods lasting multiple months, and the expense is considerable. Even then, there’s no guarantee that a hack won’t occur, as seen with multiple projects like Audius.
Finally, <1% of TVL in DeFi is insured, making the problem much worse. This not only makes retail afraid to participate on-chain, but almost becomes a non-starter for non-crypto institutions to enter the space.
Considering the above, more proactive, scalable security tooling seems like a necessity for DeFi and crypto more broadly.
While early, two types of projects excite me:
- Automated bug engines – instead of relying on bug bounties or smart contracts, OS libraries like Echidna and engines from white hat hacker DAOs like pwnednomore seem to be addressing a pretty clear need: constantly and cheaply identifying bugs throughout the dev process.
- Better testing – simulation-based testing from projects like Tenderly places far greater stress on a protocol vs. deploying on a testnet to identify potential bugs, attack vectors, etc. before deploying on mainnet.
Unlike web2, failures in crypto don’t result in the loss of somewhat inconsequential personal data, but rather millions of dollars that can’t be recovered. It could be someone’s last straw, leading them to give up on crypto.
Better security isn’t a trend but an existential problem for the sector that needs to be resolved.
**